Docker issues a separate user group on Linux systems, and those who have user accounts that aren’t added to it won’t be able to connect to it. Keep in mind that adding a user account to the Docker group is functionally root equivalent since the daemon is always running as the root user. This might be expected on a single-user Ubuntu Server system, but it will certainly be something to keep in mind for those running Docker on Arch, Fedora or Debian.
Method 1: Checking Docker Service Status
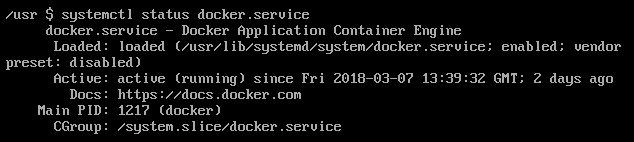
While it almost certainly is, you’ll need to check if the Docker service is currently running. At a terminal window, run systemctl status docker.service as a normal user. You should get some information about which PID number Docker’s daemon got assigned. If you don’t, then you’ll need to restart the service. Should you have restarted it, try doing whatever it was that threw you the “cannot connect to the Docker daemon” error. If it now works, then you just didn’t have the service running and don’t really need to worry about anything else besides the reason it wasn’t running. Unfortunately, this doesn’t work in a majority of cases so you’ll need to move on in those situations.
Method 2: Adding Users to the Docker Group
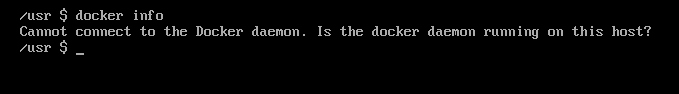
Run docker info from the command line, which will normally give you the “cannot connect to the Docker daemon” error once again. If this is the case, then you’ll need to run sudo groupadd docker; sudo usermod -aG docker $USER to add yourself to the proper group. Should this give an error because you don’t have usermod, then you can modify the command to run as sudo groupadd docker; sudo gpasswd -a $USER docker, but this generally shouldn’t be an issue because most commercial-grade Linux distributions are working with the same set of tools. In any case, run newgrp docker so you can get logged into the new docker group if you’re not already. Keep in mind this will always add the user you’re currently logged in as, which shouldn’t be too much of a problem on most people’s systems who don’t have multiple accounts beyond the one user and the root account. Since you have administrative access keyed in for the time being, run sudo chgrp docker /usr/bin docker; sudo chgrp docker /var/run/docker.sock to fix the permissions on the docker socket and command. Usually, the socket file belongs only to the root user so this will correct that. After having run it, you shouldn’t have any trouble because it now belongs to the same group that you had created in the previous command. You’ll want to test to ensure that docker runs without sudo, though, so type docker run hello-world as a regular user to make sure you’re not getting any other errors. At this point, very few users will still be receiving any sort of error message. Most things should be corrected at this point, but if you’re still having problems you might want to completely log out. Try opening another terminal emulator window, but if this doesn’t work it sometimes help to bring the system down for a complete restart if that’s at all feasible
Method 3: Using ACLs to Modify Docker Metadata
If you don’t want to belong to a group that makes you like a root user, then you can set the socket file to work with only certain permissions. You can ignore the gpasswd process if you’d prefer to do it this way. Having to scan the file system for different ACL entries in a burden for those doing a security audit, but it prevents you from having to use the docker group entirely. Should you want to do it this way, then you can run sudo setfacl -m user:name:rw /var/run/docker.sock while replacing user and name with the appropriate labels. This grants permission to access the Docker socket at /var/run/docker.sock, which should work with Debian and Ubuntu Server.
[FIX] Cannot Connect to the Docker Daemon at ‘unix:///var/run/docker.sock’What is Microsoft AU Daemon?Fix: 421 cannot connect to SMTP ServerFix: Cannot find a Valid Peer Process to Connect To